-
 IAM and GDPR: Identity Management at the Service of Compliance
IAM and GDPR: Identity Management at the Service of Compliance -
 Compliance and risk management: simplify cybersecurity and unlock your potential...
Compliance and risk management: simplify cybersecurity and unlock your potential... -
DORA SIMPLIFIED INTERACTIVE MATRIX
-
 Prepare the future: Secure your AI-Driven applications
Prepare the future: Secure your AI-Driven applications
Designed to power your digital autonomy
Europe’s trusted alternative for Identity and Access security
EUROPEAN | FREEDOM | TRUSTED PARTNER
European
In a world dominated by extra-European tech giants offering a global cybersecurity platform, WALLIX focuses on providing an alternative Identity & Access Management (IAM) platform aligned with European values that matter to customers.
Freedom
Customers have the freedom to choose their deployment model, ensuring that the Identity and Access (IAM) platform is tailored to their specific vertical needs and business context (healthcare, manufacturing, government, …)
Trusted Partner
Born in this high-stakes environment, WALLIX IAM platform is purpose-built to protect organizations where failure is not an option. With built-in compliance capabilities, WALLIX helps customers meet stringent regulations such as NIS2, GDPR, IEC 62443, DORA and beyond.
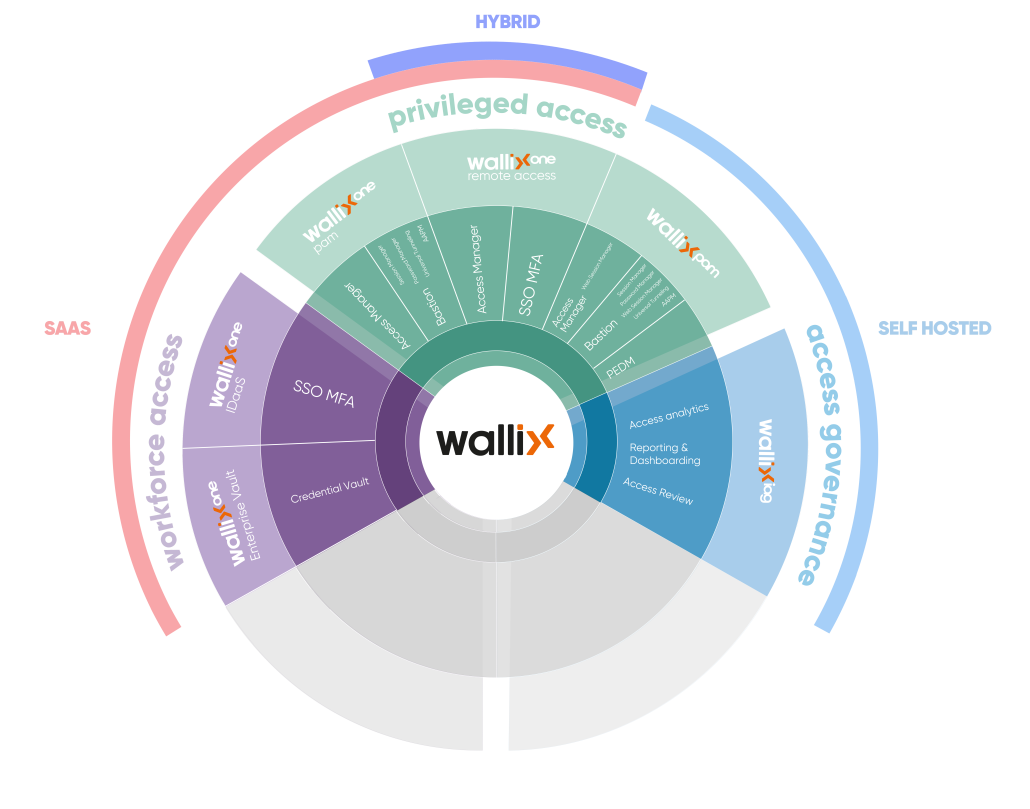
AAPM: Application to Application Password Management • IDaaS: Identity-as-a-Service • MFA: Multi-factor authentication
PEDM: Privilege elevation and delegation management • PAM: Privileged Access Management • SSO: Single sign-on
WORKFORCE ACCESS
Seamlessly securing all access
WALLIX enhance security and user experience by streamlining access with SSO & MFA and centralizing and encrypting sensitive identity data for secure sharing.
PRIVILEGED ACCESS
Controlling privileged accounts
WALLIX safeguard critical IT assets by managing privileged accounts, often targets for major breaches, and controlling remote access to maintain security while enabling seamless interaction with third-party providers.
ACCESS GOVERNANCE
Access reviews and entitlement control
WALLIX enhances access governance by providing a comprehensive mapping of identities to their respective permissions, acting as a control tower for overseeing access certification campaigns and tracking staff changes across all business applications.
Safeguarding customers across the globe
Our Partner Network
WALLIX Partners help organisations reduce cyber risks, embrace innovation and disruptive technologies securely, manage flexibility and cost, and improve operational resilience.
Simplify your cybersecurity with WALLIX and ensure your most critical systems are protected from internal and external threats.