Strengthen fraud prevention with rigorous controls, policies,
and identity monitoring within your organization.
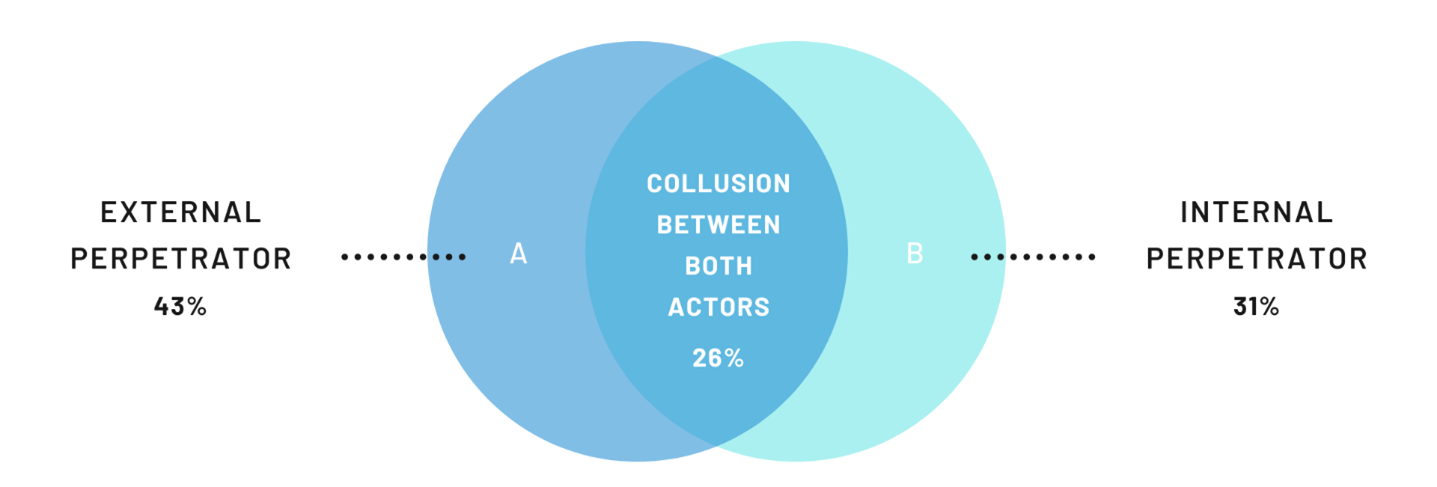
of surveyed organizations say they experienced fraud in the past two years, the highest level in 20 years of research.*
Cyber-crime is a predominant type of fraud experienced by organizations of all sizes.
of large enterprises will newly implement identity-proofing tools to address common weaknesses in workforce identity life cycle processes.**
*Sources: PwC’s Global Economic Crime and Fraud Survey 2022, **5 Key Predictions for Identity and Access Management and Fraud Detection, Gartner 2021.