Using RSA Authentication Manager for PAM
WALLIX’s Privileged Access Management (PAM) solution integrates with the RSA Authentication Manager and has just received the label RSA Ready.
Check out our new video on “adopting” the WALLIX Bastion with your RSA Authentication Manager.
Now, if you want to know the implications, consider the following:
If you like to watch war movies, you’ll invariably come across a scene where someone puts on an enemy uniform and attempts to “blend in” behind enemy lines. They’re quite often successful and able to wreak massive havoc. Cybersecurity presents its version of this scenario every hour of the day.
Who’s really who? Is the admin who just logged onto the VPN really an employee or is he or she a hacker with stolen credentials? A variety of countermeasures have evolved over the years to mitigate this risk, one of the most effective of which is two-factor authentication.
The Need for Two-Factor Authentication
Two-factor authentication requires the user to produce a second, variable proof of authenticity in order to access a resource like a network or an application. A bank ATM card is an example. Your account sign-on credentials are written onto the card’s magnetic stripe. However, you must enter your PIN to authenticate yourself before the bank will let you access your account.
Two-factor authentication is based on the premise that a simple password provides a low proof of authenticity for the user. It could be stolen or hacked. Solutions like RSA Authentication Manager force users to enter a unique, ever-changing identifier when they log in. They do it through a variety of mechanisms, including fobs and various out-of-band communications channels. This additional authentication makes it several orders of magnitude harder for an unauthorized person to penetrate the network.
Taking “Watching the Watchers” to a New Level
When users have special privileges, the need to reliably authenticate them is even more urgent. You don’t want a malicious actor getting into the administrative back ends of your network, applications, storage arrays, and data repositories. PAM is about controlling and monitoring who has access to the back end. It’s about ensuring that only authorized people can modify system settings, set up and delete accounts, and so forth.
PAM already answers the security question, “Who’s watching the watchers?”, but RSA integration takes that answer to a new level. Now, you can know if your privileged users are who they claim to be. In other words: we can authenticate the watchers who are watching the watchers. Security teams can be more confident in the effectiveness of their PAM solutions when they know privileged users have to authenticate themselves using RSA two-factor authentication.
How RSA Authentication Manager Connects to the WALLIX Bastion
Organizations that rely on RSA Authentication Manager can require users of the Bastion to authenticate themselves with RSA before being allowed access to the solution. As a result, only users who are able to authenticate themselves with two-factor authentication can use WALLIX Bastion to manage and monitor privileged account sessions.
WALLX Bastion is a comprehensive PAM solution that can be deployed across cloud and on-premises infrastructure. It sets up a single gateway with a single sign-on for access by system admins, regardless of their location or corporate affiliation.
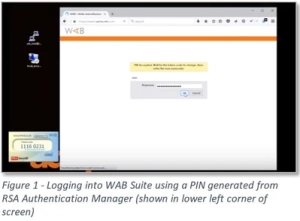
The Bastion can be configured to provide RSA SecurID two-factor authentication using the RSA Authentication Manager’s RADIUS services. The integration is seamless. Figure 1 shows the final result of the integration. The privileged user gets a unique digital PIN from the RSA widget shown at the lower-left corner of the screen. He or she can then copy and paste the PIN into the Bastion log-in screen.
Once logged in, the privileged user can use WALLIX Bastion to define and enforce access policies for admins as well as for the employees who need system access. Privileges can be granted or revoked. He or she can also monitor privileged access sessions and report on what actions were taken by privileged users. The Bastion can now even further utilize RSA authentication for each device or application by forwarding an SSH key using the RSA format by activating the SSH forward agent option.
Advantages of RSA-PAM Integration
Integrating RSA authentication with Privileged Access Management gives an organization an extra layer of control over privileged access. The integration provides a strong correlation between user identities and privileged sessions, tying the organization’s overall RSA identity authentication system of record with privileged account access. It cuts the risk of an unknown person acting as an administrator of a system. In order for an outsider to mount an attack, he would have to penetrate both the RSA system and the PAM solution — a multi-tiered approach to security that offers powerful defense in depth.
RSA is clearly one of the premier providers of truly secure two-factor authentication and WALLIX is thrilled to announce our seamless integration with their solution. Read more about the RSA-PAM integration, and discover more of our Technological Alliances.


