Maintaining Visibility Over Remote Access with Session Management
Remote access is no longer an “option” for organizations, it is a necessity for both IT and business operations. Remote access is required by your own employees as well as by third-party service providers like software vendors, support teams, and consultants.
Remote access is necessary for businesses to run operations, both for their own employees and for third-party service providers.
Although necessary, using remote access puts your organization at a higher risk for security breaches. A lack of visibility over these user sessions also makes it difficult to meet regulatory compliance and maintain control over your entire security infrastructure.
Issues with Remote Access visibility
When utilizing remote access solutions many organizations forget to consider the additional security aspects that need to be in place. Organizations need to maintain control and visibility over both local and remote user sessions.
Existing Solutions
Existing security solutions for managing remote access are lacking:
- Little control over access rights: Many solutions offer simple access rights management, essentially limited to giving user accounts or IP addresses either unrestricted access or no access. Not being able to specify more granular access rights makes it extremely difficult to maintain control over your critical data and systems. For example, a user may need to access certain data, but while you want them to be able to read some, you do not want them to be able to modify others. Without granular access rights capabilities, this is basically impossible. Plus, with some basic access solutions, you’re forced to give an entire IP address access rights, increasing your security risk vulnerability.
- Visibility and traceability: Current solutions have minimal monitoring options when it comes to overseeing user sessions and actions. Default logging capabilities often only include login and logout information. Although this can be helpful in limited situations, organizations need to be able to track every action that occurs during a session. Without this information, organizations have no understanding of how or when breaches occurred and may have trouble providing the information necessary to meet compliance regulations.
Current solutions just don’t provide the comprehensive control and visibility organizations need to maintain strong security operations.
Almost every recent data breach has involved some type of unauthorized remote access. If the privileged accounts that are used to access systems remotely are compromised by outside hackers or malicious insiders, it is critical that you can see every action that was taken.
Solve Remote Access Challenges with Session Management
What is Session Management?
Session management is a tool that allows organizations to monitor and record the access and actions of all users, including those that are utilizing remote access technologies. By monitoring all activity in real-time, you can maintain control and visibility over everything going on within your organization. The WALLIX PAM solution specifically provides additional advanced capabilities that support enterprises in ensuring complete security over their most critical systems and data.
Session management allows organizations to monitor and record the actions of all users, including those that utilize remote access.
Session Management Features
The WALLIX Session Manager allows you to complete the following for both direct and remote access:
- Control privileged accounts and access governance: Only administrators have direct access to accounts. They also have the ability to create embedded context-relevant access rules for specific systems and data.
- Real-time visibility: Unlike less sophisticated options, the WALLIX solution provides real-time visibility over all privileged users and their actions. The session manager can also be programmed to immediately terminate sessions and alert security teams when suspicious activity occurs.
- Complete audit logs: The WALLIX solution provides comprehensive searchable session information that includes all actions. In addition, all session data is recorded as videos which are then searchable using OCR (optical character recognition) technology.
Session Management Benefits
By taking advantage of the WALLIX session manager, organizations can:
- Easily meet compliance regulations
- Maintain complete control and visibility over all sessions
- Improve incident response times and processes
- Understand who has access to critical data and systems
- Keep current workflows and processes
- Prevent insider attacks, privileged account escalation, remote access problems
The Complete WALLIX Solution
Session management is just one component of WALLIX’s comprehensive security offerings. WALLIX offers the WALLIX PAM, a complete privileged access management (PAM) solution that helps organizations secure and controls the systems their organization utilizes. The Bastion can be deployed quickly and integrates with your organization’s existing security. Its scalable architecture makes it easy for both SMBs and Enterprises to utilize. The complete WALLIX PAM solution includes session management, plus:
- Password manager: Allows organizations to secure all passwords in an encrypted vault. By removing direct password access from remote access users and on-premise users, there is less risk that passwords would be shared and misused.
- Access Manager: Enterprises can centralize access to all systems and data in one easy-to-use interface. Administrators have the ability to customize many components of the solution including file classification, file transfer options, and more.
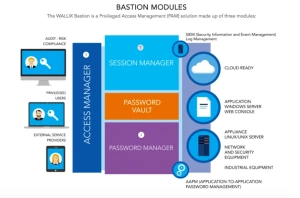
The complete WALLIX PAM helps organizations improve security and incident response.
Using all of these tools together can help your organization get a better handle on security. With the WALLIX PAM, you finally have complete visibility and control over all users, including those that access your systems remotely.
Interested in learning more about the WALLIX PAM? Contact us!


