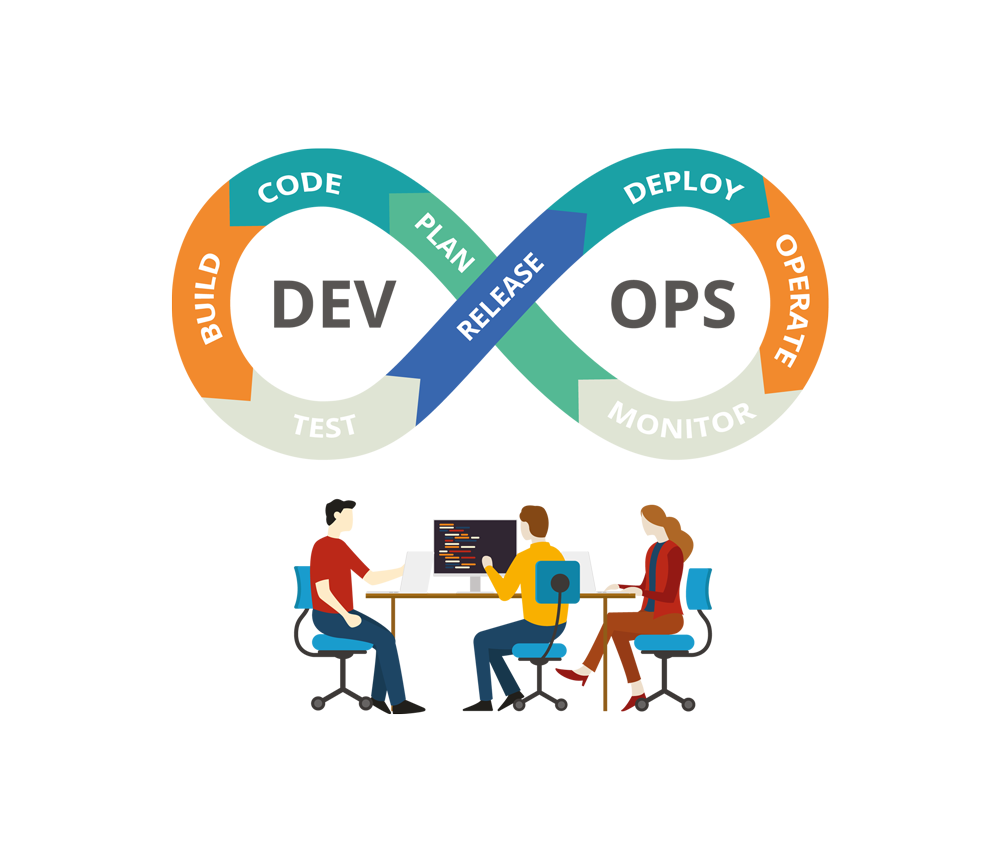
Cultivate a fortified and controlled environment, ensuring smooth operation of the DevOps and CI/CD pipelines.
of organizations worldwide will have experienced attacks on their software supply chain by 2025.*
is the monetary impact software supply chain cyberattacks will have in the global economy by 2026.**
represents the average year-over-year increase in open-source software (OSS) supply chain attacks between 2019 and 2022.
*Sources: 7 Top Trends in Cybersecurity for 2022, Gartner (2022), **Juniper Research “Vulnerable Software Supply Chains are a Multi-billion Dollar Problem” (2023), ***Source: Growth in open-source software supply chain attacks 2020-2022, Statista (2023).