SUPPORT
ABOUT
WALLIX provides cybersecurity solutions for simple, secure and trusted access, to protect digital and industrial environments. Quality and security are therefore at the heart of our concerns.

Would you really wear sockets with flip-flops to walk on a nice sandy beach? The same thing goes with SSH agent-forwarding: using a socket can sometimes be inappropriate.
SSH agent-forwarding – to keep it short, it is a mechanism providing a major advantage to a system administrator. Thanks to a local agent, users can connect to a remote server by bouncing on an intermediate server using their own private key, stored only on their computer.
But the question is:
The answer is pretty simple. If you consider the security problem posed by external connections, it’s easy to recognize that no reasonable IT manager would allow direct connections to critical resources from the internet.
The SSH agent-forwarding mechanism allows users to connect smoothly to a server by bouncing on an intermediate one and without storing the user’s private key on this intermediate server.
So, circling back to the footwear topic, SSH agent-forwarding presents a vulnerability A socket is open on the intermediate server, which represents an important vulnerability.
The socket created through SSH agent-forwarding is a well-known vulnerability.
To understand this, let’s decompose the process:
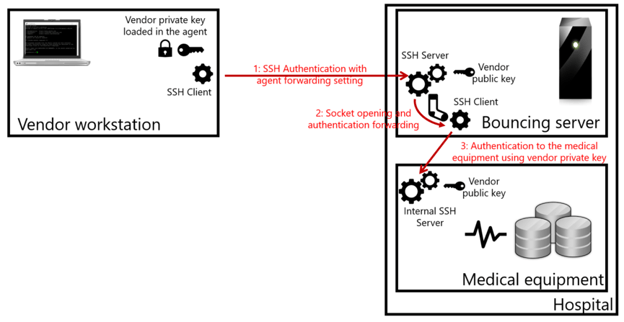
What makes the socket vulnerable? A malicious user authenticated on the bouncing system can easily divert the socket to impersonate the original user and connect to authorized servers.
Let’s get practical, now.
You are the IT manager of a hospital. Some equipment such as scanners or analyzers is managed by vendors who require secure and exclusive access to that equipment. They are not willing to share the authentication keys to those critical systems. Still, you want to be able to monitor and record every action realized on the equipment, at least for compliance purposes.
WALLIX Bastion is the ideal solution to this type of challenge. Thanks to its internal agent-forwarding solution, vendors can access their equipment from the internet using their own private key and without sharing them with the Bastion. Moreover, the Bastion works as a reverse proxy, using protocol break and not providing shell access to users.
That means no socket and no vulnerability.
In addition, the WALLIX Bastion provides a full audit arsenal so that IT administrators can keep an eye (or 4-eyes as we call it) on what is going on on their critical equipment while ensuring compliance.
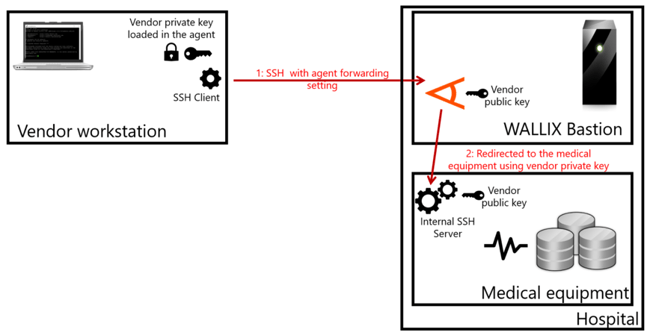
All in all, picking up the adapted footwear is that easy and can avoid serious security damage and spare your reputation.
Interested in knowing more? Contact us for a free demo!
WALLIX provides cybersecurity solutions for simple, secure and trusted access, to protect digital and industrial environments. Quality and security are therefore at the heart of our concerns.
| Cookie | Duration | Description |
|---|---|---|
| IDE | 1 year 24 days | Used by Google DoubleClick and stores information about how the user uses the website and any other advertisement before visiting the website. This is used to present users with ads that are relevant to them according to the user profile. |
| test_cookie | 15 minutes | This cookie is set by doubleclick.net. The purpose of the cookie is to determine if the user's browser supports cookies. |
| VISITOR_INFO1_LIVE | 5 months 27 days | This cookie is set by Youtube. Used to track the information of the embedded YouTube videos on a website. |
| Cookie | Duration | Description |
|---|---|---|
| __hstc | 1 year 24 days | This cookie is set by Hubspot and is used for tracking visitors. It contains the domain, utk, initial timestamp (first visit), last timestamp (last visit), current timestamp (this visit), and session number (increments for each subsequent session). |
| _ga | 2 years | This cookie is installed by Google Analytics. The cookie is used to calculate visitor, session, campaign data and keep track of site usage for the site's analytics report. The cookies store information anonymously and assign a randomly generated number to identify unique visitors. |
| _gid | 1 day | This cookie is installed by Google Analytics. The cookie is used to store information of how visitors use a website and helps in creating an analytics report of how the wbsite is doing. The data collected including the number visitors, the source where they have come from, and the pages viisted in an anonymous form. |
| hubspotutk | 1 year 24 days | This cookie is used by HubSpot to keep track of the visitors to the website. This cookie is passed to Hubspot on form submission and used when deduplicating contacts. |
| trackalyzer | 1 year | This cookie is used by Leadlander. The cookie is used to analyse the website visitors and monitor traffic patterns. |
| Cookie | Duration | Description |
|---|---|---|
| __hssc | 30 minutes | This cookie is set by HubSpot. The purpose of the cookie is to keep track of sessions. This is used to determine if HubSpot should increment the session number and timestamps in the __hstc cookie. It contains the domain, viewCount (increments each pageView in a session), and session start timestamp. |
| bcookie | 2 years | This cookie is set by linkedIn. The purpose of the cookie is to enable LinkedIn functionalities on the page. |
| lang | session | This cookie is used to store the language preferences of a user to serve up content in that stored language the next time user visit the website. |
| lidc | 1 day | This cookie is set by LinkedIn and used for routing. |
| messagesUtk | 1 year 24 days | This cookie is set by hubspot. This cookie is used to recognize the user who have chatted using the messages tool. This cookies is stored if the user leaves before they are added as a contact. If the returning user visits again with this cookie on the browser, the chat history with the user will be loaded. |
| Cookie | Duration | Description |
|---|---|---|
| __cfduid | 1 month | The cookie is used by cdn services like CloudFare to identify individual clients behind a shared IP address and apply security settings on a per-client basis. It does not correspond to any user ID in the web application and does not store any personally identifiable information. |
| __hssrc | session | This cookie is set by Hubspot. According to their documentation, whenever HubSpot changes the session cookie, this cookie is also set to determine if the visitor has restarted their browser. If this cookie does not exist when HubSpot manages cookies, it is considered a new session. |
| cookielawinfo-checbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| JSESSIONID | session | Used by sites written in JSP. General purpose platform session cookies that are used to maintain users' state across page requests. |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |
| Cookie | Duration | Description |
|---|---|---|
| _gat_UA-12183334-1 | 1 minute | No description |
| AnalyticsSyncHistory | 1 month | No description |
| CONSENT | 16 years 9 months 23 days 12 hours 13 minutes | No description |
| UserMatchHistory | 1 month | Linkedin - Used to track visitors on multiple websites, in order to present relevant advertisement based on the visitor's preferences. |
| wp-wpml_current_language | 1 day | No description |
| Cookie | Duration | Description |
|---|---|---|
| YSC | session | This cookies is set by Youtube and is used to track the views of embedded videos. |