Uniting Identity Access Management (IAM) and PAM for Cohesive Identity Governance
This month marks the 25th anniversary of the famous “On the Internet, no one knows you’re a dog” cartoon appearing in The New Yorker. Oh, how true that was, and still is, a quarter-century later. Chances are, artist Peter Steiner had no idea how prescient his drawing was. We are indeed in the Internet dog days, of identity access management (IAM) and PAM at least.

Peter Steiner, New Yorker Cartoon
Who is Who? The Essence of Identity Governance and Identity Access Management
User identity is at the root of virtually all cyber security measures. The issue is more urgent today than ever before. It’s not just who is a dog and who isn’t. It’s who works for a hostile nation-state actor? It’s who is a former employee with a grudge? And on and on. Every security control must be built upon answers to the following critical identity questions:
- “Who is who?”
- “Is the user who he or she (or it) claims to be?”
- “Can you trust them?”
- “With what can you trust them?”
This is the provenance of identity governance.
Identity Governance
Identity governance is the IT discipline that oversees who is who in an organization as well as who is allowed to do what. For example, Mr. X can use System A? How about System B? No, he cannot. However, Ms. Y can use Systems A and B. Identity governance comprises systems, policies, and processes that keep on top of user identity, authentication, and system authorization. It also includes the management of privileged users, those who have permission to administer system settings.
In practical terms, identity governance involves the use of solutions for Identity and Access Management (IAM) and Privileged Access Management (PAM). To understand how identity governance works (or how it could work better), it’s first necessary to understand how IAM and PAM function.
Understanding the Available Tools
What is Identity and Access Management (IAM)?
IAM is about two connected but distinct factors of user identity. First, an IAM solution has to be able to authenticate the user. This is the “Is this person really who they say they are?” question. However, authenticating the user is only part of the IAM process. The solution must also confirm the user’s authorization(s).
- Users are who they say they are
- Which systems/tools a specific user has access to
If it’s helpful, consider an analogy to boarding a plane. When you show your passport to the TSA, that’s authentication. It proves you’re you. But, you will still need a ticket to board the plane. That’s authorization. Logging in with Microsoft Active Directory is like showing your passport to the TSA. It verifies your identity. Signing in to Microsoft Exchange Server is like showing your ticket to get on the plane. This is also known as access control. You can’t access the plane without a ticket. You can’t access Exchange without authorization.
Ideally, the IT department has configured IAM to control access to all IT resources. These include applications, databases, storage resources, and networks as well as resources belonging to partners. IAM platforms thus mitigate security and compliance risks that can arise from unauthorized access.
What is Privileged Access Management (PAM)?
A privileged user is someone who has the right to log into the administrative back end of a system. With this access, the privileged user may be allowed to set up, modify or delete other user accounts. He or she may have the privilege of being able to modify system configurations or even uninstall the whole thing. In some cases, privileged users can access data stored on the system as well. Privileged access is sometimes referred to as “root access.”
Privileged access poses a number of potential security threats. A malicious actor impersonating a privileged user, for example, could disrupt an organization badly by eavesdropping, changing production data, or taking systems offline. A PAM solution mitigates such risks.
Privileged Access Management solutions work by establishing a secure, streamlined way to authorize and monitor all privileged users. Features typically include the ability to grant and revoke privileged access. They can act as an intermediary between privileged users and the systems they manage. This way, the privileged user does not have direct, back-end access. With some solutions, like WALLIX, the privileged user does not even know the actual password to the system he or she is administering. This prevents manual overrides, a significant vulnerability.
- Comprehensive control over who has access to critical systems
- Complete visibility into all user activity
- Password encryption and management to enforce robust password policies
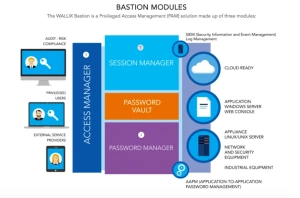
How IAM and PAM Work Together
IAM and PAM Challenges
Most organizations have an IAM solution like Active Directory. And, they will have some way of doing PAM, if not a full PAM solution. There is a risk, however, that IAM and PAM will operate as siloes. You can easily have inconsistent access policies between IAM and PAM solutions. For instance, while IAM may require reviews of user privileges, PAM may not. This is more common than you might imagine, especially if PAM is loosely managed.
IAM and PAM Best Practices
The best practice is to bring IAM and PAM together for unified identity governance. The mechanics of this unification are varied. In some cases, it might be simple coordination of access policies across the two solutions. More advanced options include integration between IAM and PAM.
A joint IAM-PAM solution centralizes identity governance, merging privileged access management with a single, authoritative identity store. Benefits of this approach include having a single point of control for provisioning all identity access in the organization, spotting users with excessive access rights, simplifying user onboarding and off-boarding, and enabling auditors to review potential inconsistencies in access controls and violations of policy.
The WALLIX-AXIAD Solution
WALLIX has made a move toward an integrated IAM-PAM solution through its partnership with AxiadIDS. The WALLIX Bastion PAM solution now combines with AxiadIDS’ Trusted Identity and Access Platform. WALLIX sees that only authorized users have access to sensitive accounts, applications, and devices. At the same time, it monitors and manages their permissions and actions. In concert, the Axiad platform verifies the identity of these authorized users. It ensures they can be trusted through authentication with a mix of credentials and identity proofing. The solutions complement each other, providing a holistic approach to security through an integrated solution.
Interested in learning more about how you can improve access control over your most critical systems, data, and devices? Contact us to learn how WALLIX can help.


