What is the Cyber Assessment Framework (CAF)?
A practical approach to resilience for the UK’s most essential organisations
Whether you’re powering national infrastructure, delivering public services, or regulating an entire sector, your ability to withstand, respond to, and recover from cyber threats defines your operational credibility.
For organisations at the heart of the UK’s critical functions, resilience must be structured, measurable, and aligned with evolving regulatory pressures, enter the Cyber Assessment Framework (CAF), developed by the National Cyber Security Centre (NCSC), CAF provides a practical way to assess, communicate, and strengthen your cybersecurity posture.
In this article, we break down how CAF works, what it expects, and how CISOs, compliance leaders, and risk officers can use it to demonstrate readiness in a high-stakes digital landscape.
Why Cyber Resilience Needs a Common Language
Cyber resilience isn’t abstract anymore. It’s tied to national stability, public confidence, and business continuity. But for many organisations operating essential services, answering the question “How secure are we?” has often resulted in vague, inconsistent, or unprovable answers.
The Cyber Assessment Framework solves this by giving organisations — and their regulators — a common structure to assess cyber maturity, backed by government authority, and adaptable across industries.
What Is the Cyber Assessment Framework (CAF)?
A tool for assessing and improving cyber resilience
At its core, the Cyber Assessment Framework (CAF) is a set of 14 security and resilience outcomes, grouped under four high-level objectives. It provides a structured approach to help organisations:
- Understand what good cyber resilience looks like
- Benchmark themselves using Indicators of Good Practice (IGPs)
- Identify gaps and prioritise remediation efforts
- Report meaningfully to boards, regulators, and stakeholders
The framework is outcome-focused rather than control-driven — allowing flexibility in how organisations meet expectations based on their size, complexity, and sector.
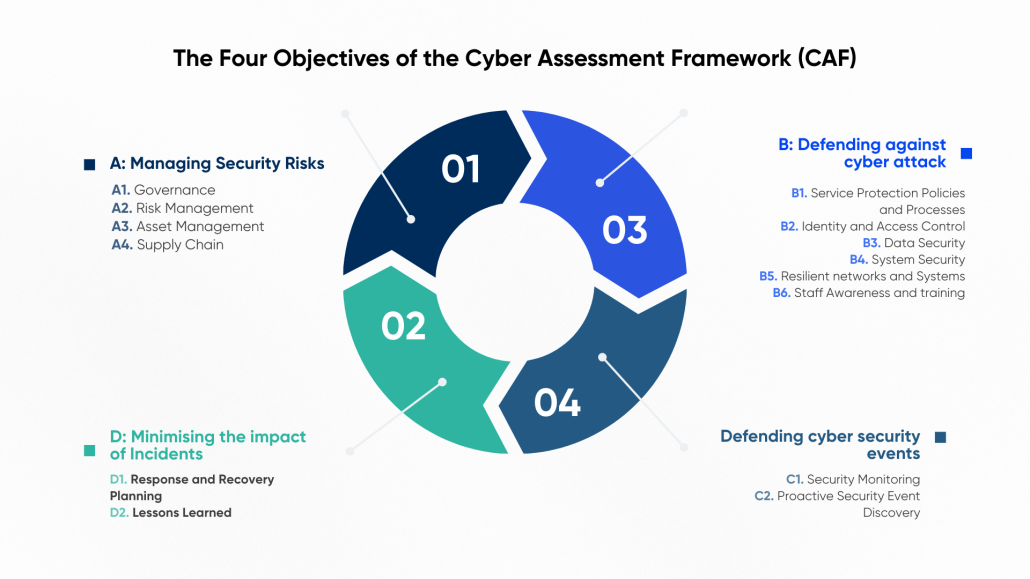
Figure 1: CAF at a Glance: Four Objectives, Fourteen Outcomes
Who Is CAF For?
The CAF is not limited to critical infrastructure operators — though they are the primary audience. It is specifically designed for:
- Organisations subject to the UK NIS Regulations
- Operators of Essential Services (OES)
- Public sector bodies delivering core functions
- Organisations managing risks to public safety
- Regulators and cyber oversight bodies
- Sectors looking to adopt a formal maturity model for cybersecurity
If your organisation supports a function where failure has national, economic, or public safety consequences, CAF isn’t optional — it’s foundational.
The Four Objectives of CAF Explained
- Managing Security Risk
This pillar focuses on governance, asset management, and supply chain assurance. Organisations must demonstrate clear ownership of cyber risk and embed it in business decisions.
- Protecting Against Cyber Attack
Here, the emphasis is on layered defences, access control, secure configuration, and ongoing vulnerability management. It’s where traditional cyber hygiene lives — but with higher stakes.
- Detecting Cyber Security Events
Detection capabilities must be proportionate to the threats an organisation faces. This includes monitoring systems, log analysis, and defined thresholds for alerting.
- Minimising the Impact of Incidents
It’s not just about prevention — it’s about recovery. This objective ensures organisations can respond, learn, and return to normal operations with minimal disruption.
Each of these objectives is backed by detailed Indicators of Good Practice, allowing organisations to self-assess or be assessed consistently.
How CAF Aligns with NIS and NIS2
As the UK modernises its cyber regulatory environment, CAF is emerging as the reference model for NIS and NIS2 alignment. NIS2 introduces stricter enforcement, broader sector coverage, and direct accountability for cyber failures.
CAF helps organisations:
- Prepare for audit and regulatory review
- Show continuous improvement over time
- Translate board-level cyber discussions into actionable maturity models
- Reduce ambiguity in third-party assessments or supply chain obligations
For regulators and oversight bodies, CAF enables sector-wide visibility, benchmarking, and risk triage — vital in a world of limited resources and growing threats.
Why European Regulatory Experience Matters
Many of the principles underpinning CAF — from governance and supply chain assurance to detection and incident response — echo those found in the EU’s NIS2 Directive. Having helped organisations across Europe operationalise compliance in some of the most tightly regulated sectors, we bring practical insight into what works at scale, how to adapt best practices across frameworks, and how to turn regulation into long-term resilience. That experience can accelerate your CAF journey.
Getting Started with CAF: A Pragmatic Approach
If you’re new to CAF, here’s how to begin:
- Define Your Scope
What systems, services, and teams are in scope? Start with your critical functions and work outward.
- Use the IGPs to Self-Assess
Each outcome includes detailed indicators. Mark yourself as “Achieved,” “Partially Achieved,” or “Not Achieved” — and collect evidence.
- Prioritise Outcomes Based on Risk
You don’t need to tackle everything at once. Focus on areas where failure would have the most impact — or where visibility is weakest.
- Communicate Progress
Use CAF results to build credible reports for internal stakeholders and external regulators. It creates transparency — and confidence.
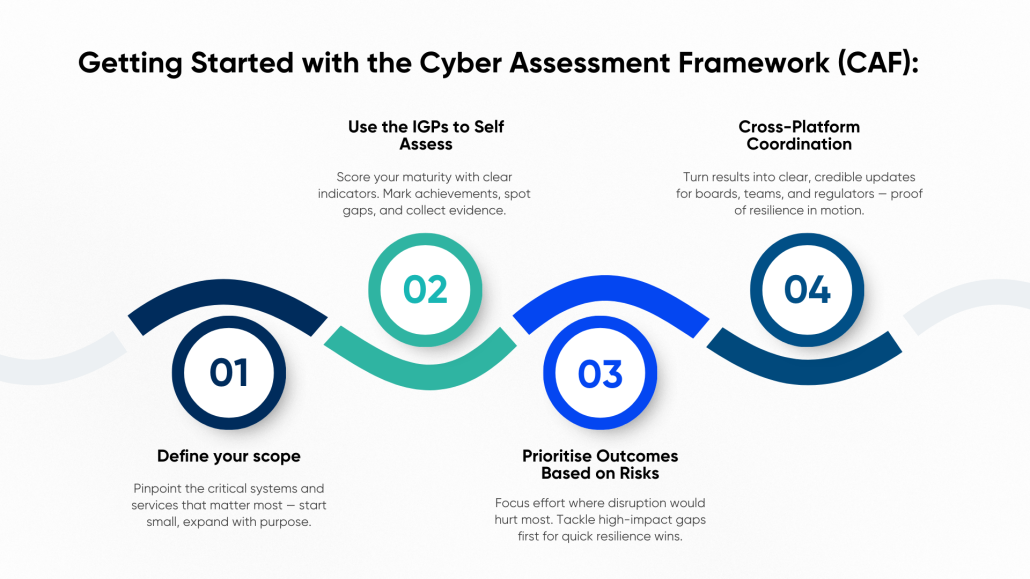
Figure 2 CAF: First Steps to Implementation
CAF as Strategy, Not Just Structure
The CAF isn’t about ticking boxes. It’s about making cyber resilience part of how your organisation works — not just how it responds in a crisis. In a time when the line between a security incident and a national event is thinner than ever, frameworks like CAF help you stay prepared, prove your maturity, and recover faster.
And for regulators and oversight bodies, CAF isn’t just a tool — it’s the basis for sector-wide stability.
Related resources
How to embed CAF in your organisation ?
Whether you’re just starting out or looking to align with NIS2 regulations more effectively, our experience supporting compliance across Europe can help.
Get in touch for strategic guidance or help integrating CAF into your cyber maturity programme.
-
 Efficient and Secure: How to Enhance OT Operations with Remote...
Efficient and Secure: How to Enhance OT Operations with Remote... -
 WALLIX One Console: A Single Control Point to Scale PAM...
WALLIX One Console: A Single Control Point to Scale PAM...



