Cyber Essentials Certification : Strengthen Your Cyber Security Baseline
Cyber threats are a constant reality for UK organisations—from small businesses to large enterprises. As of January 2024, around 50% of UK businesses reported experiencing disruptive cyberattacks or breaches in the past year—a sharp rise from 39 percent in 2022 (Statista, 2024). Recognising this growing risk, the UK government has made cyber resilience a national priority, introducing clear standards to help organisations strengthen their defences. One of the most accessible and impactful of these is Cyber Essentials, a government-backed certification that sets a baseline for cybersecurity best practices.
Built around five core technical controls, Cyber Essentials is designed to protect against the most common forms of cyber-attack—the kinds that often exploit simple misconfigurations or out-of-date systems. Whether you’re aiming to improve internal security, build trust with customers, or qualify for public sector contracts, certification demonstrates a clear, verifiable commitment to cyber hygiene.
What is Cyber Essentials?
Cyber Essentials is a UK government-backed cyber security certification developed to help organisations defend against the most common—and most preventable—cyber threats. It’s managed by IASME and endorsed by the National Cyber Security Centre (NCSC), forming part of the UK’s broader strategy to improve national cyber resilience across public and private sectors.
The scheme focuses on implementing a small set of fundamental security controls that can significantly reduce your organisation’s risk exposure. These controls are straightforward to apply and are relevant to businesses of all sizes and sectors.
To make it accessible to organisations of varying needs and maturity levels, the scheme offers two tiers of certification:
- Cyber Essentials – A self-assessed certification verified by an external body. It confirms that your organisation has implemented the required technical controls.
- Cyber Essentials Plus – A more rigorous version that includes an independent audit and technical testing to validate your defences.
Both levels help demonstrate to clients, partners, and regulators that you take cyber security seriously—and that your organisation is aligned with widely recognised best practices.
Who is Cyber Essentials for?
Cyber Essentials is designed for any organisation that wants to strengthen its cybersecurity posture—regardless of size, sector, or technical maturity. Whether you’re a small business with limited IT resources or a large enterprise looking to meet supply chain requirements, Cyber Essentials offers a clear, achievable path to reducing cyber risk.
It’s especially relevant for:

Figure 1 Cyber Essentials is particularly relevant for SMEs, public sector suppliers, organisations handling sensitive data, and IT service providers. Source: IASME, 2024.
Why It Matters: Key Benefits of Certification
In cyber security, the simplest mistakes often lead to the biggest problems. That’s exactly what Cyber Essentials is designed to prevent—by helping organisations lock down the basics before attackers can exploit them.
It’s about showing that your organisation understands the value of proactive, measurable security. Here’s why it pays off:
- Block the obvious (and the dangerous)
Most successful attacks don’t rely on sophisticated techniques—they exploit basic oversights. Cyber Essentials helps eliminate those gaps, protecting against up to 80% of common threats. - Put your security where your reputation is
Customers, partners, investors—they all want to know you take security seriously. Certification makes that commitment visible and verifiable. - Insurance that sees you coming
Some insurers reward certification with lower premiums or built-in cyber liability cover, especially for SMEs. It’s another way Cyber Essentials reduces your exposure—on paper and in practice.
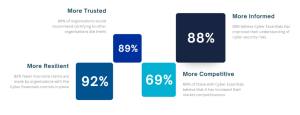
Moreover, the benefits of Cyber Essentials go beyond compliance—they deliver measurable impact across resilience, trust, competitiveness, and awareness. Organisations that certify report fewer cyber incidents, improved confidence among stakeholders, and stronger positioning in the market. The statistics below highlight some of the key outcomes experienced by certified organisations.
Figure 2 Statistics sourced from IASME’s overview of Cyber Essentials benefits, 2024.
Core Requirements: The Five Technical Controls
Cyber Essentials focuses on one powerful idea: get the basics right, and you’ll block most of what’s out there. The certification is built around five technical controls that, while simple on paper, make a big difference in practice.
Here’s what’s under the hood:
- Firewalls
Your first line of defence. Firewalls control who gets in and out of your network—because not every connection deserves a warm welcome. - Secure Configuration
Default settings are for demos, not real-world security. This control ensures systems are hardened from the start, reducing unnecessary risk. - User Access Control
Not everyone needs access to everything. This control enforces the principle of least privilege, so users only see what they need—and nothing more. - Malware Protection
Malicious software still finds its way in. With proper protection in place, you can detect and block malware before it spreads or causes damage. - Security Update Management
Patching might not be glamorous, but it’s one of the most effective things you can do. This control ensures systems are up to date and vulnerabilities are closed before attackers can find them.
These aren’t complicated technologies; they’re well-known, proven practices. What Cyber Essentials does is ensure they’re implemented consistently and effectively, across your entire organisation.
From User Access Control to PAM: Strengthening Privileged Access
Among the five technical controls in Cyber Essentials, User Access Control plays a particularly critical role. It ensures that users only have access to the data, systems, and functions necessary for their role—nothing more. This not only limits potential damage from compromised accounts but also aligns with the core principle of least privilege.
But while basic user access control protects general users, what about administrators, developers, or third-party vendors—those with elevated access and greater risk? That’s where Privileged Access Management (PAM) comes into play.
While Cyber Essentials establishes the importance of limiting user access, Privileged Access Management (PAM) takes this a step further by focusing on the accounts that pose the greatest risk—those with elevated permissions.
Admin accounts, IT personnel, and third-party vendors often hold keys to critical systems. If compromised, these accounts can cause widespread damage. PAM helps organisations enforce stricter controls by:
- Isolating and monitoring privileged sessions to detect suspicious activity
- Providing time-bound or just-in-time access rather than always-on admin rights
- Eliminating shared credentials and improving accountability through user-specific logging
In short, PAM operationalises the principle of least privilege at a deeper level, supporting compliance with Cyber Essentials while laying the groundwork for more advanced certifications like Cyber Essentials Plus or ISO 27001. Understanding administrative access governance principles helps organizations build upon Cyber Essentials foundations with more sophisticated privileged access controls.
How to Get Certified: Step-by-Step
Getting Cyber Essentials certified is refreshingly straightforward—and that’s part of its appeal. The goal is to get your cyber foundations in order, not to overcomplicate the process.
Here’s how most organisations approach it:
- Define your scope
Decide which parts of your organisation are covered by the certification—ideally, your whole business. - Conduct a gap analysis
Assess your current setup against Cyber Essentials requirements and identify where improvements are needed. - Implement the controls
Put the five core technical controls in place, ensuring they’re applied consistently across all systems in scope. - Train your team
Raise internal awareness so everyone—from IT to end users—understands their role in maintaining security. - Submit your assessment (or prepare for the audit)
For Cyber Essentials, complete the self-assessment questionnaire. For Plus, get ready for a technical audit by an external assessor.
Bidding for UK Government Contracts: Why Certification Helps
The benefits of Cyber Essentials go beyond internal security. For many UK businesses, it also unlocks new commercial opportunities—particularly in the public sector. As the UK government strengthens its cyber supply chain, certification has become more than just a best practice; in many cases, it’s a baseline requirement for doing business.
If your organisation works with—or wants to work with—the public sector, Cyber Essentials is often essential.
- Mandatory for many government contracts
Certification is a minimum requirement for contracts that involve handling personal information, financial data, or providing IT services to government bodies. Organizations handling sensitive personal data must also consider data protection with privileged access to ensure compliance with both UK government standards and European data protection regulations.
- Essential for Ministry of Defence (MOD) supply chains
Even subcontractors must hold valid Cyber Essentials certification to be eligible for MOD-related work.
- A competitive advantage in a crowded market
Certification proves your security posture is aligned with government standards—something that often tips the scales in a competitive bid.
- Signals maturity and risk management
Beyond the checklist, certification demonstrates a proactive approach to risk, which is increasingly scrutinised during procurement.
- Insurance perks for SMEs
For qualifying small businesses, certification may include automatic cyber liability insurance, reducing risk both for your organisation and the contracting authority.
- Growing relevance in the private sector
Large enterprises, especially those in finance and critical infrastructure, are beginning to adopt Cyber Essentials as a supply chain benchmark, further broadening your opportunity base.
Whether you’re targeting government tenders or aiming to become a trusted supplier in a regulated sector, Cyber Essentials helps open doors—and keeps them open.
Timeline and Renewal
Getting Cyber Essentials certified doesn’t have to be time-consuming—but it does require focus and preparation.
- Cyber Essentials (self-assessment):
Most organisations complete the self-assessment process within 1 to 3 weeks, depending on how close their current setup is to the standard and how quickly they can implement any required changes. - Cyber Essentials Plus (audit-based):
If you’re aiming for the Plus certification, allow for several additional weeks. This includes preparing for the technical audit, resolving any findings, and coordinating with an external assessor. - Annual renewal:
Certification isn’t a one-and-done achievement. To keep it valid—and maintain eligibility for certain contracts or insurance benefits—you’ll need to renew annually, ensuring your controls continue to meet evolving standards.
Conclusion
Cyber Essentials won’t solve every cyber challenge—but it’s one of the most practical, high-impact moves an organisation can make. It sends a clear signal: you take security seriously, and you’re willing to prove it.
In a digital environment where trust is earned through action—not promises—this certification helps you show up prepared. Whether you’re safeguarding critical data, working toward regulatory alignment, or positioning your business for new opportunities, Cyber Essentials is where credibility begins. Organizations seeking further information security standard adoption often find that Cyber Essentials provides an excellent foundation for progressing to more comprehensive frameworks like ISO 27001.
Related resources
-
 Efficient and Secure: How to Enhance OT Operations with Remote...
Efficient and Secure: How to Enhance OT Operations with Remote... -
 WALLIX One Console: A Single Control Point to Scale PAM...
WALLIX One Console: A Single Control Point to Scale PAM...



