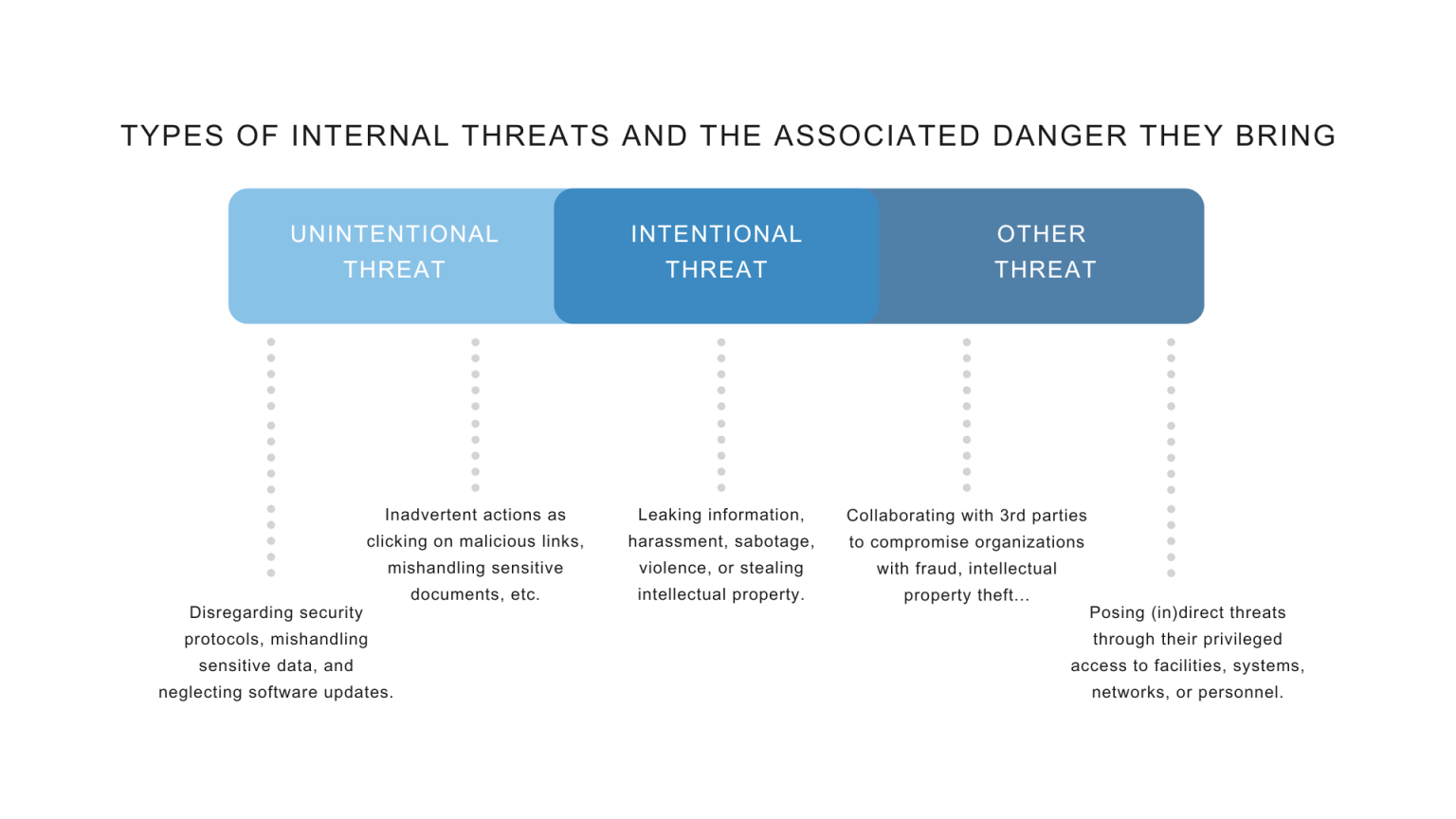
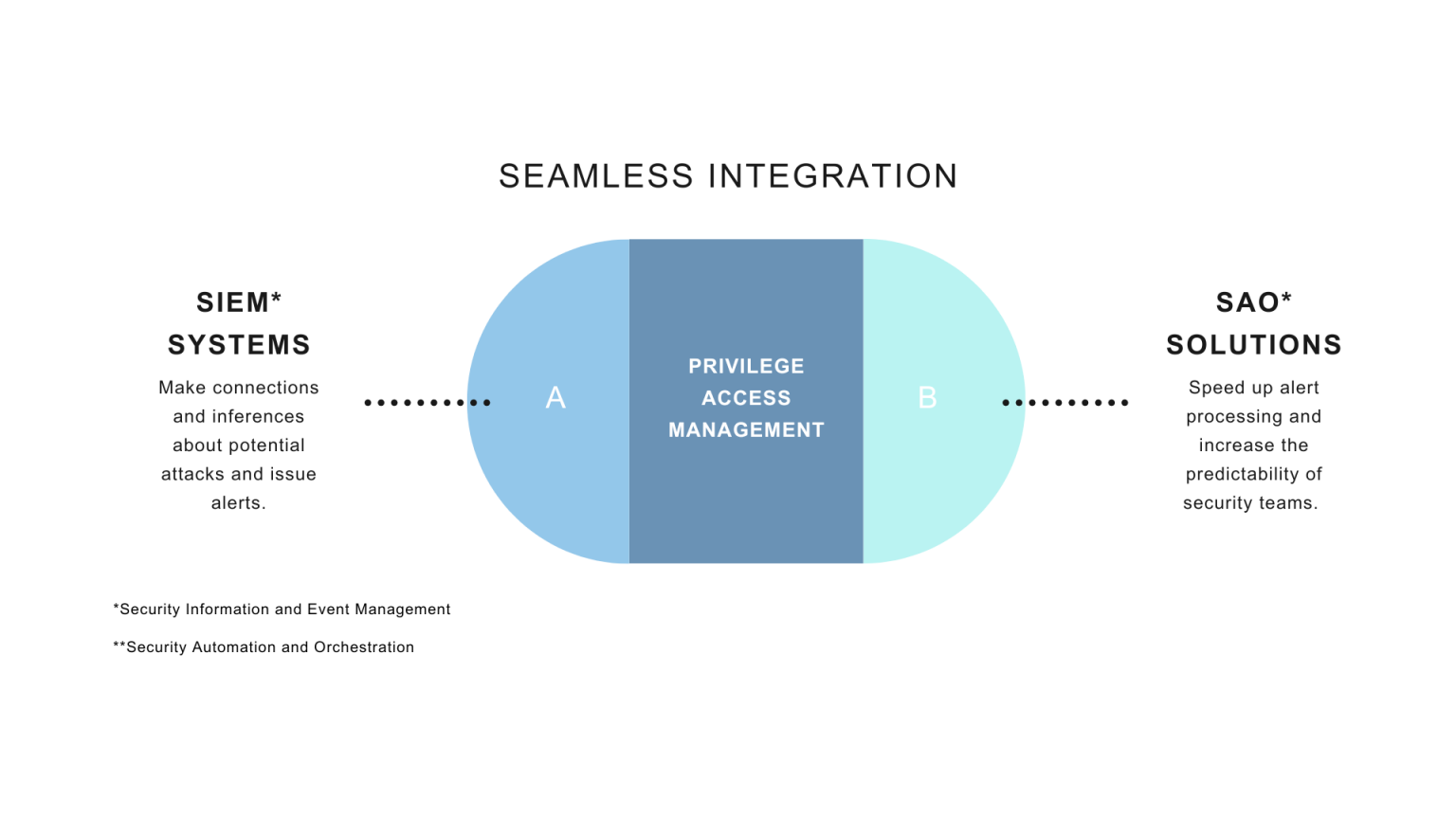
Implement robust tracing and monitoring mechanisms for your entire workforce, ensuring comprehensive protection.
of participants said that detecting and countering insider attacks has become increasingly challenging in the cloud.*
was the average cost of an insider threat situation in 2022.**
is the number of days it takes for an insider threat scenario to be noticed and 75 days on average to be controlled.***
*Source: Cost of Insider Threats Global Report, Ponemon Institute 2022 , **Source: Insider Threat Report, Cyber Security Insiders 2023, *** Source: Insider Threat Mitigation Guide, CISA 2020